Microsoft has highlighted a growing security threat identified as Storm-2372, linked to a series of cyberattacks targeting various sectors since August 2024.
These attacks have affected government bodies, NGOs, IT services, defense, telecommunications, healthcare, academia, and energy sectors across Europe, North America, Africa, and the Middle East.
The threat actor, believed to have ties to Russian interests, employs messaging platforms like WhatsApp, Signal, and Microsoft Teams to impersonate notable figures to gain the trust of their targets.
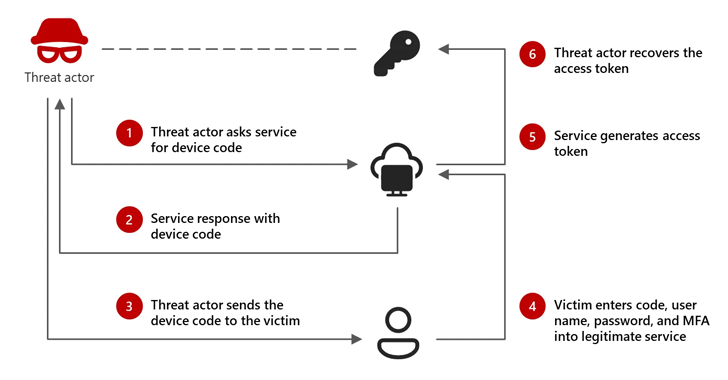
According to Microsoft’s Threat Intelligence, the attacks utilize a phishing method known as “device code phishing,” which tricks users into logging into productivity applications. The attackers capture the login tokens to access compromised accounts.
These authentication codes are leveraged to infiltrate target accounts, collecting sensitive information and maintaining access as long as the tokens are valid. Microsoft reports that attackers often send phishing emails disguised as Microsoft Teams meeting invites, prompting recipients to authenticate through a device code generated by the attacker, enabling them to hijack the authenticated session.
The process involves tricking victims into inputting a legitimate device code on a valid sign-in page, which provides the attackers access to authentication tokens, allowing them to breach the target’s accounts and data effortlessly.
To mitigate risks associated with these cyberattacks, organizations should restrict device code flow where feasible, implement multi-factor authentication resistant to phishing, and adhere to the principle of least privilege to enhance their security posture.